Intelligent video surveillance technology uses computer vision technology to analyze the video image content of the surveillance scene, automatically detect abnormal conditions in the surveillance screen, and alert and provide useful information, so as to more effectively remind security personnel to deal with illegal intrusions in a timely manner.
At present, intrusion detection algorithms commonly used in intelligent video surveillance technology are interframe difference method, background subtraction and optical flow method. They detect moving targets from video sequences to implement intrusion alarms. However, these algorithms focus on the study of moving object detection in a video scene, and the monitoring system is often monitored simultaneously in multiple regions. To this end, an implementation method for intelligent intrusion alarm in multi-region video surveillance system is presented. The method adopts hybrid Gaussian background modeling motion detection algorithm, OpenCV, multi-threading and other technologies to realize the effective detection and alarm function for intrusion targets.
1 Hybrid Gaussian background modeling motion detection algorithm Hybrid Gaussian background modeling The motion detection algorithm is one of the subtractive background motion detection algorithms. The subtractive background motion detection algorithm obtains the moving target area by differentiating between the current frame and the background image. The requirements of this algorithm for background images are: 1) no moving targets; 2) constantly updated to adapt to changing backgrounds. There are many methods for constructing background images. The hybrid Gaussian background modeling algorithm is one of the typical ones. The algorithm has better adaptability to the changing environment.
1.1 Mixed Gaussian Background Modeling Defines K states for each pixel in a video frame, each state being represented by a Gaussian distribution function. Some of these states represent the pixel values ​​of the background, while the other represents the pixel values ​​of the foreground. If the pixel value of each pixel is represented by the variable Xt, its probability density function can be described by K Gaussian distribution functions, as shown in equation (1): 
1.2 Hybrid Gaussian background modeling parameter update When obtaining the pixel value It at a certain point t, firstly, the sequential similarity detection algorithm is used to detect that the Gaussian distribution function matches the current pixel value It, and the steps are as follows:
1) setting the deviation threshold T;
2) Select the Gaussian distribution function whose mean μi, t is closest to the pixel value It, and detect whether the absolute value of the difference between the two is smaller than Tσi, t-1, if |It-μi, t-1| ≤ Tσi, t- When 1 is established, it is determined that the Gaussian distribution function matches the current pixel value, and the relevant parameters are updated according to the equations (2) to (4); if |It-μi, t-1|≤Tσi, t-1 does not hold, then the determination is made. The Gaussian distribution function does not match the current pixel value, and the Gaussian distribution function with the smallest weight is replaced by a new Gaussian distribution function. The new Gaussian distribution function mean μi, t is It, the standard deviation σi, t is the maximum initial standard deviation, and the weight ωi,t is the minimum initial weight. 
In the formula, α is the model learning rate, which is used to control the correction speed of the weight ωi, t; Ï is the parameter learning rate, which is approximately Ï≈(α/ωi, t).
3) Other Gaussian distribution function parameters are unchanged, and only their weights are normalized.
1.3 Background Pixel Judgment The mixed Gaussian background modeling algorithm determines whether the state represented by the Gaussian distribution function represents the background pixel value by calculating the value of ωi,t/σi of each Gaussian distribution function in the model. The higher the value, the more likely it is the background pixel.
2 mixed Gaussian background modeling intrusion detection
OpenCV is an open source function library for image processing and computer vision developed by Intel Corporation based on C/C++ language. Most of these functions are optimized code based on the Intel processor instruction set to maximize processor performance.
OpenCV has powerful image and matrix computing capabilities and is an ideal tool for secondary development of computer vision and image processing.
OpenCV provides a hybrid Gaussian background modeling function whose main functions are as follows: 
Function: Initialize the mixed Gaussian background model with one frame of image data.
Parameters: first_frame models the first frame of image data for the mixed Gaussian background; parameters models the initialization parameters for the mixed Gaussian background.
This paper uses the function default setting: the number of states K=5, that is, the mixed Gaussian background model contains 5 Gaussian distributions, the deviation threshold T=2.5, the model learning rate α, and the maximum initial variance. ![]() The background point determination threshold ωi, t / σi > 0.7.
The background point determination threshold ωi, t / σi > 0.7. 
Function: Update the mixed Gaussian background model.
Parameters: pFrame is the video stream frame image data for updating the Gaussian background model; bg_model is the mixed Gaussian background model pointer, and the background and foreground images can be obtained by bg_model->background and bg_model->foreground. ![]()
Function: Release the memory occupied by Gaussian background model parameters.
After the morphological processing of the foreground image, a certain size of the moving area can be detected, that is, it is determined that someone has invaded. The result is shown in Figure 1.
This article refers to the address: http://

3 video surveillance image data acquisition and conversion
3.1 Video Surveillance Image Data Capture The monitoring quality of the SDK-based video surveillance card with Tianmin's SDK-2500 is very different from that of the VFW library. Use the built-in function library to fully utilize the performance of the video surveillance card processor. The monitor quality is high and the display resolution is up to 720x576 (PAL). When using the VFW function library, the display resolution is only 320x240. The comparison of the monitored images obtained by the two methods is shown in Figure 1. In order to obtain high-resolution monitoring image quality, this paper uses video monitoring card to bring up the function library to develop video surveillance system software.
The video monitoring card comes with a function library that provides two functions for capturing the image data of the current frame. One class saves image data as a file on disk and another class copies image data to the clipboard. Since the clipboard is a memory reserved separately in the Windows system, since the memory read/write speed is more than ten times that of the hard disk, the clipboard can also avoid repeated reading and writing of the hard disk, so the image data is captured by the clipboard. ,code show as below: 
Parameter description: int n is the video monitoring card number: LPBITMAPINFO lpBI refers to the pointer of the BITMAPINFO structure; void*pDIBBits is the pointer to the bitmap data.
3.2 Conversion of DIB to IPLImage data format Since the image data format captured by the clipboard is DIB, and the basic format of the image in the OpenCV function library is IPlImage*, the DIB image data format needs to be converted to the IPLImage* image data format. The code is as follows: 
4 Multi-zone real-time motion detection The 32-bit Windows operating system runs applications in a preemptive multitasking manner. When a program runs, the operating system starts a process. In order for the process to do some work, each process must contain at least one thread. The thread is responsible for executing the code contained in the process address space. Each thread shares all process resources, including open files, signal flags, and dynamically allocated memory.
A thread is the basic entity that the system allocates CPU time. It is also the smallest unit of code execution. In fact, only one thread is running at the same time. Since the time allocated by each thread is very small (about 20 ms), the CPU frequently switches between threads by time sharing, making the system seem to have multiple programs running at the same time. .
Windows provides two kinds of threads - worker threads and user interface threads. Both threads are supported by the MFC library. User interface threads usually have windows, so it has its own message loop. The worker thread does not have a window, so it does not need to process the message.
The user interface thread is used to respond to user operations and other controls of the program. The auxiliary thread is used to capture video images of multiple regions, and uses the motion detection algorithm to implement real-time intrusion alarm function. The program flow is shown in Figure 2.

5 Experimental Results In order to verify the performance of the multi-area video surveillance intrusion detection and alarm method proposed in this paper, two SDK-2500 video surveillance cards were used to perform long-term video surveillance on both indoor and outdoor areas, and the video frame rate was monitored. 30 frames / sec. To capture a stable video image, a wait time of 100 ms has been added to the worker thread. The results of 100 alarms were randomly selected, and the results are shown in Table 1.
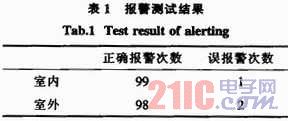
It can be seen from the test results that the indoor false alarm rate is 1% and the outdoor false positive rate is 2%. According to the saved video image analysis, the indoor false alarm occurred in the case of turning on the light, which was caused by the sudden change of the ambient brightness; the two outdoor false alarms occurred in the windy situation, due to the large swing of the branches.
6 Conclusion This article uses multi-threading technology to achieve multi-region motion detection intrusion alarm automation in video surveillance systems. The method utilizes the video monitoring card's own function library, fully exerts the performance of the video monitoring card processor, and obtains a high monitoring image quality; the method has a low false alarm rate and can be widely applied to various video monitoring systems.
Load Cell Module,Weighing Module,Weigh Modules Load Cells,Module Weighing
Xiaogan Yueneng Electronic Technology Co., Ltd. , https://www.xyeloadcell.com